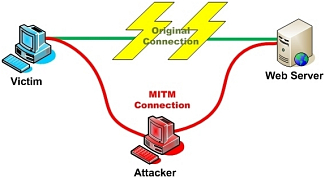
A subordinate certifcate issued by Trustwave was used to monitor people accessing SSL-protected services on a customer’s internal network
By Dan Goodin
The so-called subordinate root certificate allowed the customer to issue SSL credentials that Internet Explorer and other major browsers would accept as valid for any server on the Internet. The unnamed buyer of this skeleton key used it to perform what amounted to man-in-the-middle attacks that monitored users of its internal network as they accessed SSL-encrypted websites and services. The data-loss-prevention system used a hardware security module to ensure the private key at the heart of the root certificate wasn’t accidentally leaked or retrieved by hackers.